Encrypting data in some form is a core requirement for many solutions; however, there are different ways we can encrypt data.
The most basic is encryption at rest. Storage services in Azure use encryption at rest by default – this includes Virtual Machine disks, storage accounts, and even SQL Server. To encrypt data, Azure uses Microsoft-managed keys; however, there is the option to use keys managed by yourself. When using customer-managed keys, you need to store them in a safe place that your services can access in a tightly controlled manner – because if you can get access to the keys, you can decrypt the data.
Important note
Data encryption at rest uses a key, a randomly generated set of bits used with a mathematical algorithm to scramble data. The same key is then used to decrypt (unscramble) the data. Much like a password, the length and complexity of the key determine its strength.
As well as encrypting data at rest, virtual machines can also use additional tools such as BitLocker to encrypt the data at the operating system level. Known as full-disk encryption, this uses a separate key that is always managed by you. Again, a safe place to store and manage keys is therefore required.
Encrypting data is only one way to protect an application. Most systems must communicate with another component at some point – for example, a database or another web service. These connections are sometimes secured with a connection string, which is stored in a configuration file. This is considered insecure as the configuration file is often open and easily compromised. The most secure method is storing items like this as secrets in a safe location that can then be accessed and controlled.
Finally, encryption of data when moving between systems is essential. Encryption in transit uses an SSL/TLS certificate to encrypt data between points.
For the preceding scenarios and more, Azure offers the Key Vault service.
Azure Key Vault enables you to store, generate, and manage access to keys, secrets, and certificates. By storing sensitive data such as this in a key vault, you can control who can access a key, certificate, or secret using Azure’s built-in RBAC roles. Access is also separated between the management plane (who can administer the vault) and the data plane (who can create, read, and delete keys, secrets, and certificates).
Because a key vault is a component of your subscription, you can also limit access to the data stored within it to other components within that subscription. For example, a key vault can be locked to only allow access over an internal VNet, which would mean only devices such as virtual machines would be able to access it.
The following diagram shows an example of how you can secure access to your key vault at the network level:
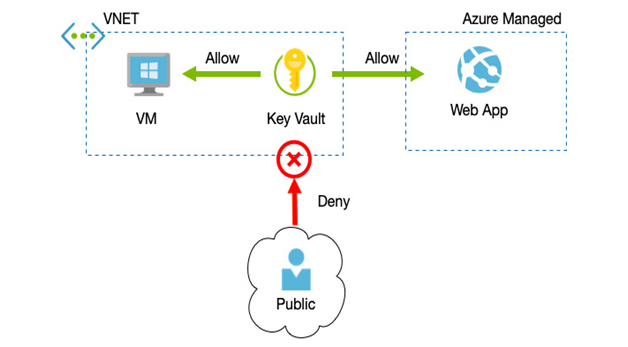
Figure 6.1 – Network-level access restrictions for key vaults
A recommended approach to any form of security is that secrets and keys are rotated regularly, for example, every 90 days.
Important note
Key rotation is a standard security strategy to protect against keys or secrets being compromised. Enforcing passwords in connection strings to be changed limits the amount of time a hacker could potentially have to access your data.
When creating a key vault, there are two pricing tiers that you can choose from, Standard and Premium. Standard encrypts data and information using software-generated keys, whereas Premium uses Hardware Security Modules (HSM) to protect your keys, which is more secure.
Everything stored in a key vault is automatically replicated to a paired region to protect your secrets, keys, and certificates to protect them from a region outage.
Finally, Azure Key Vault provides monitoring capabilities to log all actions, such as creating, reading, updating, or deleting keys, secrets, and certificates. Log entries can be sent to Azure Monitor, archived in a storage account, or streamed to an event hub. This enables any security events to be thoroughly investigated and tracked, down to the identity of who/what acted.
Next, we will run through the process of creating a key vault.